5 common data security challenges businesses face and how to overcome them

Data security has always been important to businesses, especially those that handle sensitive information. As more businesses rely on data to conduct critical activities–thanks in no small part to the shift to remote work and digital native companies— data security has become even more crucial. With all that data to protect from increasingly-complex threats, it’s no wonder that data security is top of mind for everyone.
With that in mind, today, we’ll cover the top five data security challenges we see businesses facing all the time… and how to overcome them.
The State of Data Security Today
Before we get started, let’s get the lay of the land. When it comes to cybersecurity, businesses have significantly increased spending in recent years, investing an average of $2,691 on cybersecurity per full-time employee.
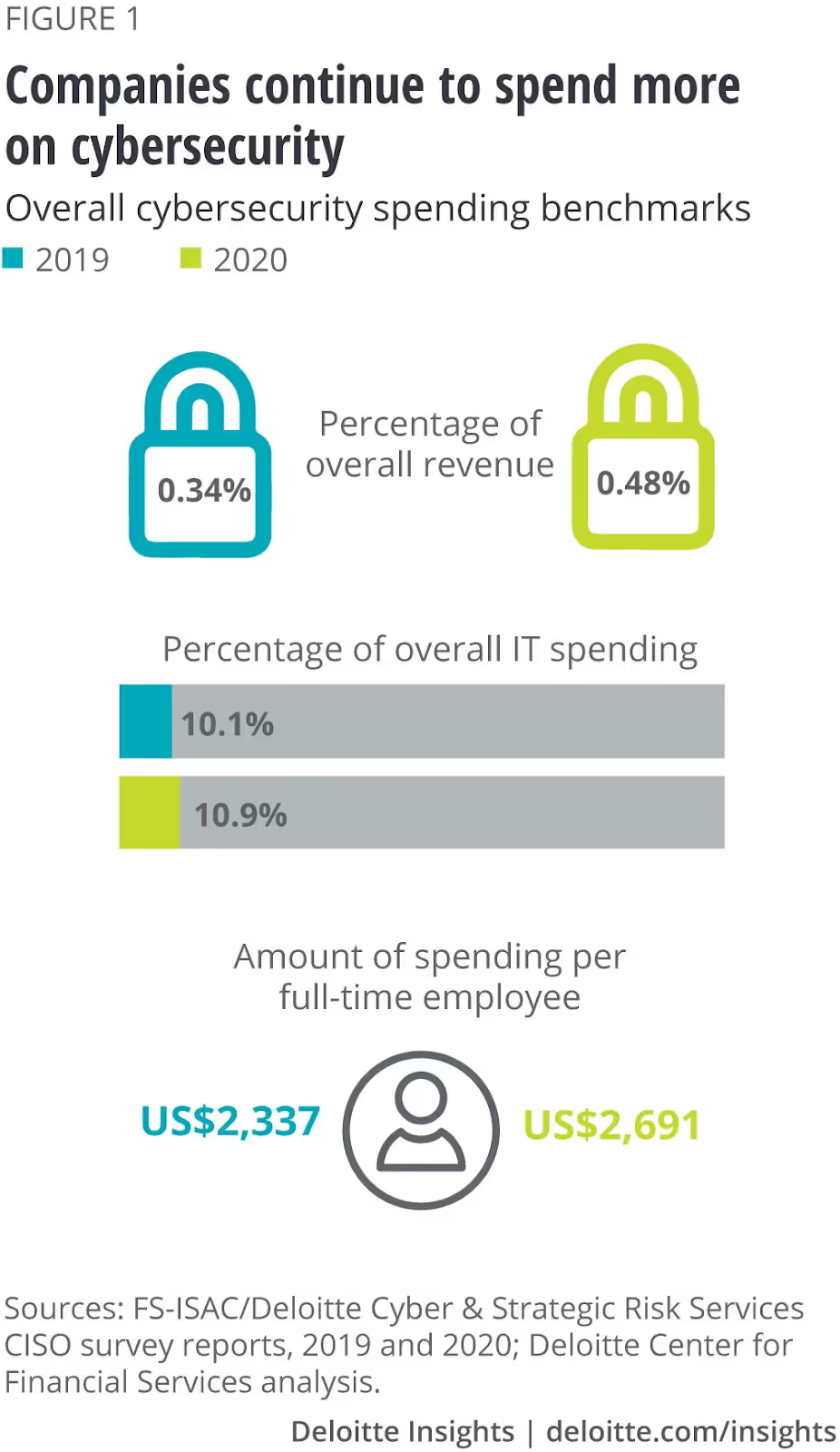
Despite this increase in spending and effort to protect data, security challenges persist. That’s why businesses need to place data security at the core of their data strategy.
Why Data Security Should Form the Core of Any Organization’s Data Strategy
While most business leaders understand the importance of data security and do what they can to plug gaps in their security infrastructure, they must be acutely aware of what a security breach would mean for their organization.
Hybrid work models have made it easy for employees to access critical business information from the comfort of their homes. However, this dependence on easy information access also means that data issues can directly impact business continuity and hamper productivity. In addition to lost productivity, businesses also stand to lose significantly in downtime costs, monetary fines, reputation loss, and more.
IBM estimates the average total cost of a single data breach to be approximately $4.24 million, representing a 10% year-over-year growth in total cost. As businesses increasingly depend on complex data systems to deliver their services or ensure uptime, these costs will only rise.

Those are some sobering statistics. But that leaves us with the question… Now what? What can we do about that?
Let’s explore.
5 Common Data Security Challenges Businesses Must Overcome
1. Data Leaders Can Lack Visibility into Their Organization’s Data Footprint
Operational teams can (and often do!) have vastly different data needs. This frequently encourages them to find and use highly specialized tools to manage their data. As a result, deeply entrenched information silos are formed.
Critical business data is spread across different departments and rarely shared or reported comprehensively. This compartmentalization prevents business and data leaders from receiving a holistic view of their organization’s data practices or even measuring the size of their data footprint.
2. Increased Regulatory Attention on Data Security Creates Constantly Evolving Compliance Requirements
Data security breaches directly impact customers and end users as much as they affect businesses. Breaches can be extremely disruptive for users who rely on continued access to business services to maintain uptime within their organizations or to complete personal tasks.
The need for secure data across organizations and industries has increased regulatory scrutiny on data processes everywhere. Businesses can struggle to maintain compliance in a rapidly changing and evolving regulatory environment.
3. Larger Data Footprint Presents a Larger Attack Surface for Malicious Actors
While businesses have evolved significantly to better integrate data processes into daily activities, cybercriminals have also evolved to take advantage of the greatly expanded attack surface this new business reality presents.
Employees regularly use repeated passwords across personal and professional devices, connect to insecure networks, and unknowingly leave attack vectors open for malicious actors. With malware becoming extremely easy to access and use, malicious actors need alarmingly little to cause significant data issues for their target.
4. High Turnover Rates and Hybrid Work Arrangements Across Industries Requires Data Teams to Manage Permissions and Access Efficiently
To maximize efficiency and reduce data storage and management costs, business departments can sometimes place highly sensitive business information in the same locations as documents that need to be accessed by employees to fulfill their daily responsibilities.
This increases the load on data teams who must individually manage privacy settings and access permissions for each team member. As workers continue to explore different work options and arrangements, modern businesses need to consider setting up differential privacy policies for data with varying levels of sensitivity to reduce the reliance on resource-intensive manual data privacy processes.
5. Businesses Choose to Take a Reactive Approach to Data Security Instead of a Proactive One
Despite an organization’s best efforts, security gaps can go unnoticed and create security or data quality issues. Businesses that fail to take a proactive approach to discover and address these concerns can find themselves spending more money and using additional resources to solve easily preventable problems. A reactive approach to data security ignores the damage that a security breach can cause in favor of damage control during a crisis when it’s already too late.
Top Tips for Modern Organizations to Improve Data Security
Now that we’ve discussed what the issues are, it’s time to talk about how to address them.
Build a Formal Long-Term Data Security Strategy
The first step in ensuring long-term data security is by establishing a strategy to manage data security concerns and challenges. This strategy should outline how the organization plans to react to the different attack and breach types and detail the processes each department should participate in to prevent any damaging breaches.
Reduce the Possible Attack Surface by Placing Additional Security Checkpoints at Vulnerable Points
Approximately two-thirds of businesses are actively taking a Zero Trust approach to managing data access and security. This approach allows businesses to limit access to sensitive data while placing additional security controls at the point of access for critical business information.

Automate Critical but Resource Intensive Data Processes
Managing data processes manually can be extremely time and resource intensive. However, data management is of extreme importance for maintaining data integrity, quality, and security. Modern data management tools allow data teams to automate repetitive but critical tasks to reduce the burden on overstretched data teams.
Each of these challenges and solutions requires businesses to take a more involved and proactive stance on data management. Sometimes, this is simply unrealistic as businesses are often forced to get by with overstretched data teams and limited data management know-how. A comprehensive enterprise data observability tool can help close this gap by allowing business and data leaders to keep their fingers on the pulse and measure the health of their most important data at all times.
Want to learn more about data security best practices and data protection in testing and development? Check out Test Data 101, your one-stop shop for learning real ways to protect sensitive customer data in testing and QA environments while increasing developer efficiency.


.svg)
.svg)





















.svg)



